Gaining Control: How To Access Your Raspberry Pi Behind A Router For IoT Projects
Ever feel like your awesome Raspberry Pi project is stuck behind a digital wall, unable to be reached when you're away from home? That feeling, a bit like being unable to access important settings on your computer when you need them, is quite common for folks building Internet of Things (IoT) gadgets. It's a real head-scratcher when you want to check on your smart garden or adjust your automated pet feeder from anywhere, isn't it?
Well, just like you might dig into the control panel on a Windows machine to tweak power plans or audio settings, there are ways to truly take charge of your Raspberry Pi, even when it's nestled safely behind your home router. This guide is all about helping you bridge that gap, giving you the freedom to manage your Pi from afar. It’s about gaining that real sense of "control" over your creations, so you can make them work for you, no matter where you are.
We'll explore several practical ways to make your Raspberry Pi accessible, turning it from a local marvel into a global utility. You'll learn how to set things up so you can truly manage your IoT devices, and frankly, it's a very satisfying feeling to know you can reach your projects whenever you wish. So, let's get your Raspberry Pi talking to the outside world, shall we?
Table of Contents
- The Router Barrier: Why It Is Tricky
- Method 1: Port Forwarding (The Direct Road)
- Method 2: VPN (The Secure Tunnel)
- Method 3: Ngrok (Instant Public Access)
- Method 4: MQTT (The IoT Messaging System)
- Method 5: Remote.it (Service for Simplicity)
- Keeping Your IoT Pi Safe and Sound
- Picking the Best Way for Your Project
- Frequently Asked Questions
The Router Barrier: Why It Is Tricky
So, you've got your Raspberry Pi humming along, maybe controlling some lights or gathering sensor data. It works beautifully when you're on your home network, doesn't it? But then you step out, and suddenly, your Pi feels like it's behind a very thick, unyielding door. This is because your home router acts like a security guard, protecting all the devices inside your network from the vast, open internet. It's a good thing, really, keeping unwanted visitors out. However, it also means your Pi can't easily "see" or "be seen" by the outside world without some specific instructions.
Your router uses something called Network Address Translation, or NAT, which basically lets many devices share one public internet address. When you try to connect to your Pi from outside, the router doesn't know which specific device inside your home you're trying to reach. It's a bit like trying to send a letter to an apartment building without specifying the apartment number; the mail just won't get to the right person. This is why you need a clever way to tell your router, "Hey, send this specific kind of traffic to my Raspberry Pi, please!" It's all about directing the flow, isn't it?
Method 1: Port Forwarding (The Direct Road)
What Port Forwarding Is All About
Port forwarding is, in a way, like creating a specific tunnel through your router's protective wall directly to your Raspberry Pi. You tell your router, "Any incoming requests on a certain 'port' – which is just a number that identifies a specific type of network traffic, like port 22 for SSH or 80 for web pages – should be sent directly to my Raspberry Pi's internal address." It's a very common method, and arguably, one of the first things people think of when trying to get remote access. This gives you pretty much direct control, you know, over your Pi from anywhere on the internet.
How It Works with Your Router
To set this up, you usually log into your router's administration page, which is often done through a web browser. You'll find a section, sometimes labeled "Port Forwarding," "NAT," or "Virtual Servers." Here, you'll specify the external port number you want to use, the internal port number (which is usually the same), and the internal IP address of your Raspberry Pi. It's really important to give your Pi a static internal IP address first, so its address doesn't change every time it restarts, otherwise, your forwarding rule would break. This process gives you, like, very granular control over network traffic.
The Good and the Not-So-Good
The biggest upside of port forwarding is its straightforwardness and often excellent performance. It's a direct connection, so there's minimal delay. However, the major downside is security. When you open a port, you're essentially creating a direct path from the internet to your Pi. This means your Pi becomes a potential target for malicious actors who are constantly scanning for open ports. If your Pi isn't properly secured with strong passwords, updated software, and a firewall, it could be vulnerable. So, while it offers direct control, it also demands a higher level of vigilance, you know, to keep things safe. It's a bit of a balancing act, really.
Method 2: VPN (The Secure Tunnel)
What a VPN Does
A Virtual Private Network, or VPN, creates a secure, encrypted tunnel between your remote device (like your laptop or phone) and your home network. Instead of opening a direct port to your Pi, you connect to your home network via the VPN. Once connected, your remote device essentially acts as if it's physically inside your home network, giving you full access to your Raspberry Pi and any other devices, just as if you were sitting right there. It's a much more private and secure way to gain control, honestly, over your home network resources.
How Your Pi Can Be a VPN Server
You can set up your Raspberry Pi itself to act as a VPN server. Popular choices for this include OpenVPN or WireGuard. This involves installing the VPN server software on your Pi, configuring it, and then setting up client software on your remote devices. When you connect to your Pi's VPN server, all your internet traffic from that remote device can be routed through your home network, making it seem like you're browsing from home. This method gives you a truly comprehensive way to access your entire home network, not just the Pi. It's quite a powerful tool, actually, for remote management.
Advantages and Drawbacks
The primary advantage of using a VPN is security. All traffic through the tunnel is encrypted, making it very difficult for others to snoop on your connection. It also means you don't have to open multiple ports on your router for different services; just one port for the VPN server is usually enough. The main drawback is the setup complexity. Setting up a VPN server can be a bit more involved than simple port forwarding, requiring some understanding of networking concepts and command-line interfaces. Also, your home internet's upload speed can affect VPN performance, especially if you're transferring large files. But, you know, for robust security, it's often worth the effort.
Method 3: Ngrok (Instant Public Access)
What Ngrok Offers
Ngrok is a service that creates a secure tunnel from a public endpoint to a locally running service on your Raspberry Pi. Think of it like this: Ngrok gives your local Pi a temporary, public web address (or URL) that anyone on the internet can use to reach it. You run a simple command on your Pi, and Ngrok handles all the tricky router configuration and firewall bypassing for you. It's a really neat way to quickly expose a web server or an SSH service running on your Pi without messing with router settings at all. It's very much a plug-and-play solution, in a way.
How It Makes Connections Easy
The process is incredibly simple. You download the Ngrok client to your Raspberry Pi, authenticate it with your Ngrok account, and then run a command like `ngrok http 80` (to expose a web server on port 80) or `ngrok tcp 22` (for SSH). Ngrok then provides you with a public URL or address that you can use from anywhere. This means you don't need to touch your router's settings, and it works even if your internet service provider uses something called "carrier-grade NAT," which often makes port forwarding impossible. It's a pretty convenient tool, honestly, for quick access.
The Upsides and Downsides
Ngrok's biggest advantage is its ease of use and quick setup. It's perfect for testing, sharing a project with someone, or getting temporary access. You don't need a static IP address, and it handles the router issues. However, the free tier provides random, temporary URLs, meaning the address changes every time you restart the Ngrok tunnel. For a persistent address, you'd need a paid plan. Also, you're relying on a third-party service, so if Ngrok goes down, your access goes down too. While it's great for convenience, it's not always the best for long-term, mission-critical IoT deployments where absolute control is paramount. But for many, it's a really solid option, you know, for getting started.
Method 4: MQTT (The IoT Messaging System)
Understanding MQTT's Role
MQTT, or Message Queuing Telemetry Transport, isn't about directly accessing your Pi's command line or a web interface in the same way the other methods are. Instead, it's a lightweight messaging protocol specifically designed for IoT devices. It works on a "publish/subscribe" model, using a central server called a "broker." Your Raspberry Pi can "publish" data (like sensor readings) to the broker, or "subscribe" to topics to receive commands (like turning a light on or off). This is a pretty fundamental way, you know, for IoT devices to communicate.
How MQTT Facilitates Communication
Instead of you directly connecting to your Pi, both your Pi and your remote control device (like your phone or another computer) connect to a public MQTT broker. When you want to send a command to your Pi, your remote device publishes a message to a specific "topic" on the broker. Your Pi, which is subscribed to that same topic, then receives the message and acts on it. When your Pi has data to send, it publishes it to another topic, and your remote device, subscribed to that topic, receives the data. This means neither device needs a direct incoming connection from the internet, solving the router barrier problem very elegantly. It's a rather indirect, yet very effective, way to manage things.
Why MQTT Is Great for IoT and Its Limits
MQTT is fantastic for IoT because it's very efficient with bandwidth and power, making it ideal for small devices like the Raspberry Pi. It's also inherently secure if you use an encrypted connection (SSL/TLS) to the broker and implement proper authentication. Many public MQTT brokers are available, or you can run your own on a cloud server. The limitation is that it's for messaging, not for full remote desktop or SSH access. You can send commands to control your Pi's functions, but you can't, for example, easily browse its file system directly using MQTT. So, while it offers control over specific functions, it's not for general system access. It's quite specialized, in some respects.
Method 5: Remote.it (Service for Simplicity)
What Remote.it Provides
Remote.it is a service that provides secure, on-demand access to your devices behind a router without needing port forwarding or a VPN. It creates a secure connection between your remote device and your Raspberry Pi through their cloud infrastructure. It's designed to be incredibly easy to set up, letting you connect to various services running on your Pi, such as SSH, HTTP, or even custom applications, with just a few clicks. It's a bit like having a concierge service for your network connections, honestly, making things really simple.
How It Simplifies Access
You install a small piece of software, called a "daemon," on your Raspberry Pi. This daemon registers your Pi with the Remote.it service. Then, from a web browser or their desktop/mobile app, you can select your Pi and the service you want to access (e.g., SSH). Remote.it then establishes a secure, peer-to-peer connection through its cloud, allowing you to connect directly to your Pi's service. It completely bypasses the need for router configuration, dynamic DNS, or static IP addresses, making it incredibly user-friendly. It’s pretty much a one-stop shop for remote access, which is quite handy.
The Benefits and Potential Costs
The main benefit of Remote.it is its unparalleled simplicity and strong security. It uses end-to-end encryption and doesn't expose any open ports on your router, significantly reducing your attack surface. It's ideal for those who want remote access without getting deep into networking complexities. There's a free tier that's usually sufficient for personal projects, but larger deployments or more advanced features might require a paid subscription. So, while it's incredibly convenient, it does introduce a dependency on a third-party service and potentially a recurring cost for extensive use. But for many, it's a very appealing solution, you know, for easy control.
Keeping Your IoT Pi Safe and Sound
No matter which method you choose for gaining remote access, security should always be a top priority. Just like you'd keep your Windows control panel settings secure, protecting your Raspberry Pi from unauthorized access is absolutely crucial. A compromised Pi could become a stepping stone for attackers to access your entire home network, or even be used in malicious activities without your knowledge. So, taking these steps is, you know, really important.
Strong Passwords and SSH Keys
The default username for Raspberry Pi OS is 'pi' with the password 'raspberry'. Change this immediately! Use a long, complex password for any user accounts on your Pi. Better yet, for SSH access, disable password authentication entirely and use SSH keys. SSH keys are much more secure than passwords, as they rely on cryptographic pairs rather than something that can be guessed or brute-forced. It's a pretty fundamental security measure, in fact, for any remote system.
Regular Software Updates
Keep your Raspberry Pi's operating system and all installed software up to date. Developers constantly release updates that patch security vulnerabilities. Running `sudo apt update` and `sudo apt upgrade` regularly will ensure your Pi has the latest fixes, helping to protect it from known exploits. This is just like keeping your Windows operating system current, you know, to avoid issues. It's a simple step, but utterly vital.
Firewall Protection
Even if you're using methods like VPNs or Ngrok, it's a good idea to enable a firewall on your Raspberry Pi itself. Tools like `ufw` (Uncomplicated Firewall) make it easy to configure rules that only allow necessary incoming connections. For example, if you only need SSH access, you can configure the firewall to block all other incoming traffic, adding another layer of defense. This acts as an extra guard, really, for your device.
Least Privilege Access
When setting up services or applications on your Pi, run them with the minimum necessary permissions. Avoid running services as the 'root' user unless absolutely necessary. Create separate, unprivileged user accounts for specific tasks. If a service running with limited permissions gets compromised, the damage an attacker can do is, you know, significantly reduced. It's a principle of security that helps manage potential risks, pretty much like giving out only the keys that are absolutely needed.
Picking the Best Way for Your Project
Choosing the right method for IoT projects to control your Raspberry Pi behind a router really depends on your specific needs and comfort level. If you prioritize maximum performance and have a good understanding of networking and security, port forwarding might be an option, but it comes with higher risks. For the best security and full network access, setting up a VPN on your Pi is a very robust choice, though it takes a bit more effort.
If you need quick, temporary access or are just testing things out, Ngrok is incredibly convenient. For pure IoT messaging and device-to-device communication, MQTT is the go-to solution, offering efficiency and scalability. And if simplicity, ease of setup, and strong security without complex configurations are your main concerns, Remote.it offers a very user-friendly experience. Ultimately, the goal is to gain effective control over your Pi, allowing you to manage your projects from anywhere, and frankly, there's a method here for nearly every situation. You can learn more about Raspberry Pi Basics on our site, which might help you decide.
Frequently Asked Questions
How do I remotely access my Raspberry Pi from outside my network?
You can use several methods, including port forwarding on your router, setting up a VPN server on your Pi, using services like Ngrok or Remote.it, or employing an IoT messaging protocol like MQTT. Each approach has its own setup requirements and security implications, so the best choice depends on your specific needs and comfort with networking. It's about finding the right path to, you know, your Pi.
Is it safe to port forward for Raspberry Pi?
Port forwarding can be safe if done with extreme caution and proper security measures. However, it exposes your Raspberry Pi directly to the internet, making it a potential target for attackers. It's absolutely essential to use strong, unique passwords, enable SSH key authentication, keep your Pi's software fully updated, and configure a firewall to restrict access to only necessary services. Without these steps, it's honestly, a rather risky approach.
What are alternatives to port forwarding for IoT devices?
Many alternatives offer greater security and ease of use compared to port forwarding. These include setting up a VPN server on your Raspberry Pi (like OpenVPN or WireGuard) to create a secure tunnel, using cloud-based tunneling services such as Ngrok or Remote.it, or implementing an IoT messaging protocol like MQTT for command and data exchange. These methods generally avoid exposing open ports on your router, which, you know, adds a significant layer of protection.
IoT Using Raspberry Pi - Pianalytix - Build Real-World Tech Projects
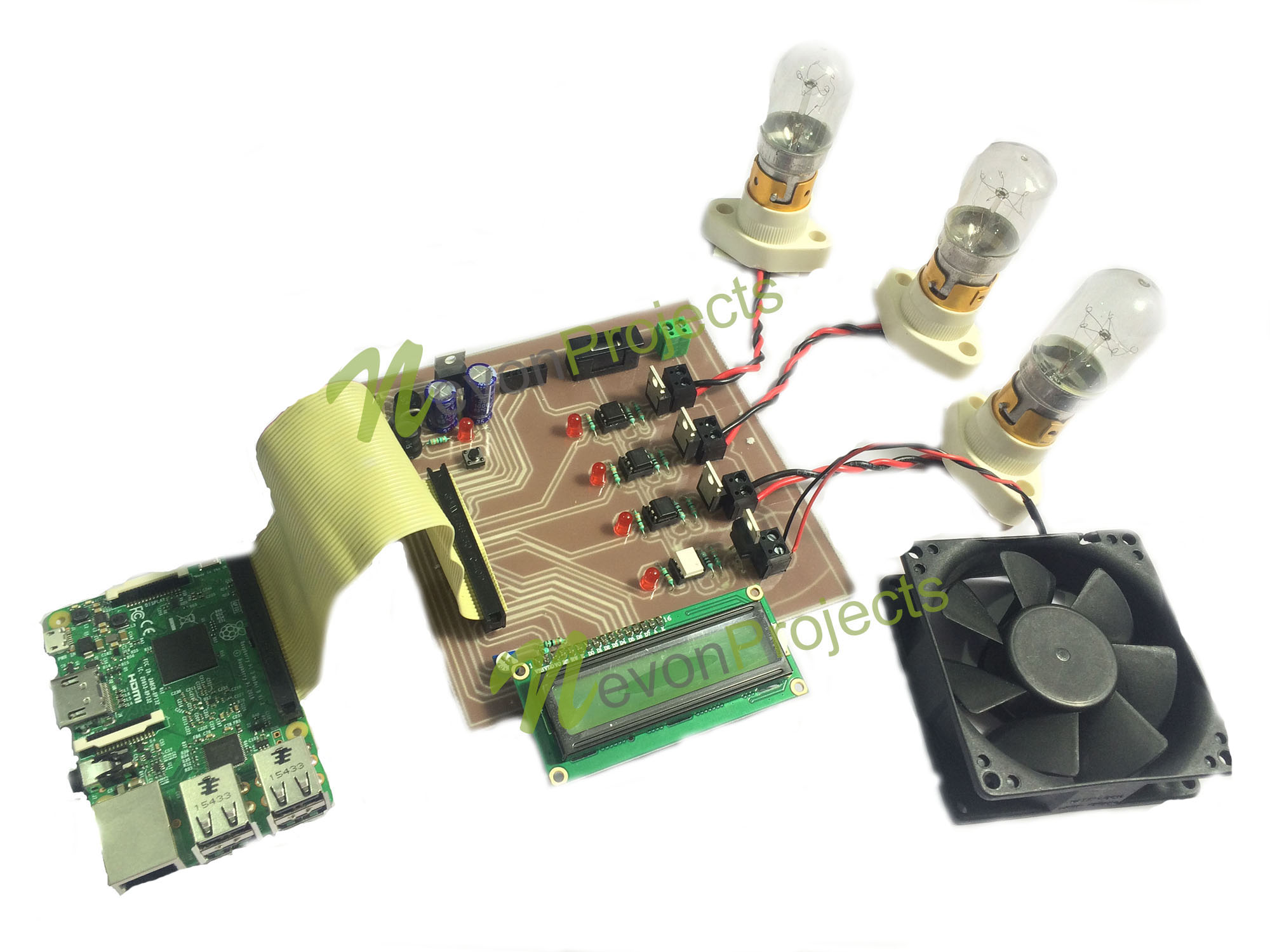
IOT Home Automation Using Raspberry Pi

IOT Industry Automation Using Raspberry Pi