Control Your Raspberry Pi Beyond The Router: Your Guide To NAT Traversal
Feeling a bit stuck when you want to reach your Raspberry Pi from outside your home? You are definitely not alone. Many folks find themselves scratching their heads, wondering why their tiny computer, so capable within the local network, seems to vanish the moment they step out the door. It's like having a brilliant helper at home, but they can't answer the phone when you're away. That feeling of being cut off, of not quite being able to take control of the situation, is a common frustration for many Raspberry Pi enthusiasts, you know?
The culprit, more often than not, is something called Network Address Translation, or NAT. Think of your home router as a very strict doorman. It lets things out easily, but it's very particular about what it lets back in, especially if it didn't specifically ask for it. This setup, while good for basic security, makes it tricky to directly connect to your Raspberry Pi from the wider internet, so it's a real puzzle for some.
But don't you worry, because there are smart ways around this. You can absolutely gain the ability to control raspberry pi behind router nat, no matter where you are. We're going to explore several clever methods, each with its own benefits and a few things to think about. It's about empowering you to access your projects, your files, or whatever your Pi is doing, whenever you need to, which is pretty neat, actually.
Table of Contents
- The NAT Nuisance: Why Your Pi Hides
- Common Paths to Remote Pi Control
- Choosing the Right Way for You
- Getting Started: Practical Steps
- Frequently Asked Questions
The NAT Nuisance: Why Your Pi Hides
So, you have your Raspberry Pi humming along, maybe running a little web server, or perhaps it's a home automation hub. Everything works fine when you're connected to your home Wi-Fi, right? But then you try to connect from a coffee shop, or from a friend's house, and suddenly, nothing. It's like your Pi has gone into hiding, which is rather frustrating, you know?
What is NAT, Really?
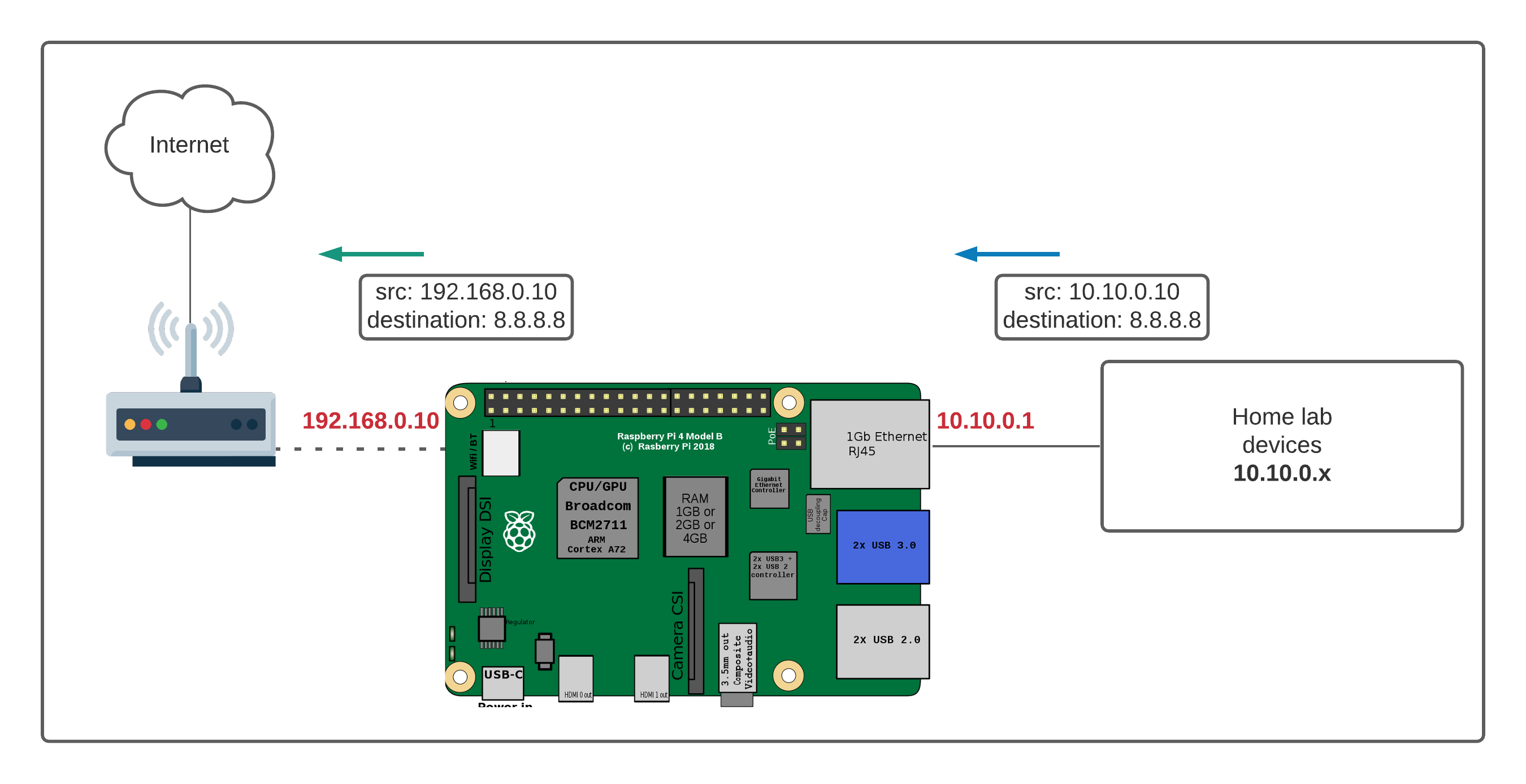
NAT, or Network Address Translation, is basically a system that lets many devices inside your home network share just one public IP address. Your internet service provider gives your router a single address, a bit like a street address for your whole house. Every device inside your house – your phone, your laptop, your Raspberry Pi – has its own private, internal address, which is more like a room number inside that house. This setup helps save public IP addresses, as a matter of fact.
When your Pi sends a request out to the internet, your router remembers that request. When the response comes back, the router knows exactly which internal device (your Pi) it needs to send that data to. This is generally how your internet works without you even thinking about it, but it creates a specific problem for incoming connections, you see.
The Wall Between You and Your Pi
The issue arises when you want to initiate a connection *to* your Raspberry Pi from outside your home. Your router, the doorman, hasn't received an outgoing request from your Pi for this specific incoming connection. So, it simply doesn't know where to send the incoming data. It sees a connection attempt from the outside world, and without a specific instruction, it just drops it, which is pretty typical behavior for security reasons. This is the "wall" that prevents you from directly accessing your Raspberry Pi, making it hard to control raspberry pi behind router nat without some extra steps.
Common Paths to Remote Pi Control
Thankfully, there are several well-established ways to get around this NAT wall. Each method has its own setup process and different levels of complexity or security considerations. It's not a one-size-fits-all solution, but you'll likely find one that fits your needs perfectly, you know?
Port Forwarding: The Direct Route
Port forwarding is a bit like telling your router, the doorman, "Hey, if anyone asks for room 22 (a specific port number) from the outside, always send them to my Raspberry Pi (its internal IP address)." You essentially create a direct path through the router for specific types of traffic. This is probably the most straightforward method for many home users, and it can be very effective for specific applications like a web server or a game server, you see.
The main thing to remember with port forwarding is that it opens a specific "door" to your internal network. While convenient, it does carry some security considerations. You are making your Raspberry Pi directly accessible to the internet, which means it needs to be properly secured. This is a very important point to keep in mind, obviously.
VPNs: Your Private Tunnel
A Virtual Private Network, or VPN, creates a secure, encrypted tunnel between your remote device (like your laptop) and your home network. When you connect to your home VPN server (which could be running on your Raspberry Pi itself, or another device on your network), your remote device effectively becomes part of your home network. It's like you're physically sitting at home, even if you're thousands of miles away, which is pretty cool, actually.
This method offers excellent security because all traffic through the tunnel is encrypted. It also lets you access *any* device on your home network, not just your Pi, through that tunnel. Setting up a VPN server on a Raspberry Pi can be a bit more involved than simple port forwarding, but it offers a much more secure and versatile way to control raspberry pi behind router nat, and so it's a popular choice for many.
Reverse SSH Tunneling: A Clever Workaround
Reverse SSH tunneling is a really clever trick that flips the usual connection on its head. Instead of you connecting *to* your Pi, your Pi initiates a connection *out* to a publicly accessible server (often a cheap VPS or another computer you control with a public IP). This connection stays open, creating a tunnel. Then, when you want to access your Pi, you connect to that public server, and it forwards your connection through the existing tunnel to your Pi. It's a bit like having your Pi call a friend (the public server) and then you call that friend to talk to your Pi, you know?
This method is great if you don't want to mess with your router's settings or if your ISP uses "carrier-grade NAT" (CGNAT), which makes port forwarding impossible. It requires an intermediate server, which adds a little bit of cost or complexity, but it's a very robust way to gain access, especially when other methods fail. You get to bypass the router's NAT without opening any incoming ports, which is a significant advantage for some users, apparently.
Cloud Services and IoT Platforms: The Easy Way Out
For those who prefer a simpler, more hands-off approach, several cloud-based services and IoT platforms can help you control raspberry pi behind router nat. Services like Dataplicity, Remote.it, or even some aspects of MQTT brokers work by having your Raspberry Pi connect *out* to their cloud servers. Then, you access your Pi through that cloud service's web interface or application. It's a bit like using a remote control app for your TV, where the app talks to a central server, and the TV also talks to that same server, which is pretty convenient.
These services often handle all the tricky networking bits for you, making them very user-friendly. They might come with a subscription fee for advanced features, but for basic remote access, many offer free tiers. They are especially good for specific tasks, like monitoring sensor data or turning things on and off remotely, and they simplify the whole process immensely, basically.
Choosing the Right Way for You
Deciding which method to use depends on your specific needs, your comfort level with networking, and how important security is to your particular setup. There's no single "best" way, as a matter of fact.
Security First: Important Thoughts
Whenever you make your Raspberry Pi accessible from the internet, security becomes a very big deal. If you choose port forwarding, you must ensure your Pi is well-protected. This means strong, unique passwords, keeping your software updated, and perhaps using a firewall on the Pi itself. Think of it like putting a good lock on that opened door, you know?
VPNs and reverse SSH tunnels generally offer a higher level of security because they create encrypted paths. Cloud services also handle much of the security for you, though you're trusting their platform. Always use strong credentials, no matter which path you choose. It's about taking control of the situation instead of feeling overwhelmed or powerless about potential risks, which is pretty important.
Ease of Use vs. Control
Port forwarding is generally simple to set up if you have access to your router's settings. VPNs and reverse SSH tunnels require more technical know-how to configure but offer greater flexibility and security. Cloud services are often the easiest to get going, but they might limit what you can do or how much data you can transfer without paying. So, you have to weigh convenience against how much direct control you want over the connection, and that's a personal choice, really.
Getting Started: Practical Steps
Let's briefly touch on what you'd generally do for each method. Remember, detailed guides are available online for each of these, so this is just a quick overview to give you a sense of what's involved, you know?
Setting Up Port Forwarding
First, you'll need to give your Raspberry Pi a static IP address on your home network. This means its internal address won't change, which is pretty important. Then, you'll log into your router's settings, find the "Port Forwarding" section, and create a rule. This rule will tell the router to send incoming traffic on a specific external port to your Pi's static internal IP address and a specific internal port. It's usually a straightforward process for most home routers, as a matter of fact.
Configuring a VPN Server
You can install VPN server software like OpenVPN or WireGuard directly on your Raspberry Pi. This involves installing the necessary packages, generating configuration files, and then setting up client software on your remote devices. It's a bit more of a project, but there are many helpful scripts and guides out there to simplify it, and so it's quite achievable for many people.
Building an SSH Tunnel
For a reverse SSH tunnel, you'll need a public server (a VPS is a common choice). Your Raspberry Pi will then use an SSH command to connect to that public server, creating the tunnel. On your remote computer, you'll then connect to the public server on a specific port, and that connection will be forwarded to your Pi through the tunnel. It's a very clever way to bypass NAT without changing router settings, you know?
Exploring Cloud Options
With cloud services, you typically sign up for an account, install a small agent program on your Raspberry Pi, and then follow the service's instructions to link your Pi to your account. From there, you access your Pi through their web portal or dedicated application. This is generally the least technical approach, making it very appealing for many, you see.
Frequently Asked Questions
You might have a few common questions bubbling up about this topic, and that's perfectly normal. Here are some answers to things people often ask, you know?
Can I access my Raspberry Pi from outside my home network?
Yes, absolutely! While your router's NAT might seem like a barrier, there are several effective methods, like port forwarding, VPNs, or cloud services, that let you reach your Pi from anywhere with an internet connection. It just takes a little setup, which is pretty much what this whole article is about, actually.
What is NAT and how does it affect my Raspberry Pi?
NAT stands for Network Address Translation. It's a system your router uses to let multiple devices in your home share one public internet address. It affects your Pi by blocking unsolicited incoming connections from the internet, meaning you can't directly connect to your Pi from outside your home unless you configure a specific pathway through the NAT, which is the challenge we're addressing, you see.
Is it safe to port forward my Raspberry Pi?
Port forwarding can be safe if done correctly, but it does expose your Raspberry Pi directly to the internet. This means security is very important. You need to make sure your Pi's operating system and any services running on it are updated, that you use strong, unique passwords, and consider implementing a firewall on the Pi itself. It's about taking proactive steps to protect your device, which is a smart thing to do, obviously.
So, there you have it. The challenge of how to control raspberry pi behind router nat is definitely solvable. Whether you choose to open a direct port, create a secure tunnel, or use a convenient cloud service, the ability to access your Pi from anywhere is within your grasp. It's about finding the method that feels right for you and your projects, and then taking the steps to set it up. Go ahead and start experimenting; your Pi awaits your remote commands, which is a pretty exciting prospect, you know? Learn more about remote access solutions on our site, and link to this page for more Raspberry Pi project ideas.

How to Turn a Raspberry Pi Into a VPN-Secured Travel Router
Someone made a Raspberry Pi router you can control with your smartphone
Control Raspberry Pi Behind Router Windows 10 Free: A Comprehensive Guide